New Phishing Tactics Used by Threat Agents in 2019 and How to Get Around Them
As internet security infrastructure becomes smarter and more difficult to penetrate, hackers have made the migration toward phishing attacks as the cyber-criminal weapon of choice because they exploit the seeming weakest part of any security system – humans!
In the first quarter of 2019, phishing attacks and other social engineering tactics like Business Email Compromise grew at a similar pace to 2018. They are still the starting point of almost all attempted and successful data breaches which cost an average of $1.23 million per breach for enterprises and an estimated $120,000 per incident for SMBs.
Phishing scams are usually associated with emails, but now they take other forms as well. As our awareness of and defences against old tactics grow, cyber-criminals explore new tricks to get through our defensive walls, which means constant vigilance is key. Below, we have outlined 4 new tactics increasingly being employed by cyber-criminals and some with incrediblesuccess.
Non-Email Phishing Attacks
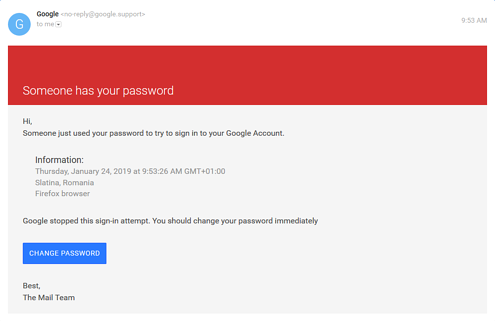
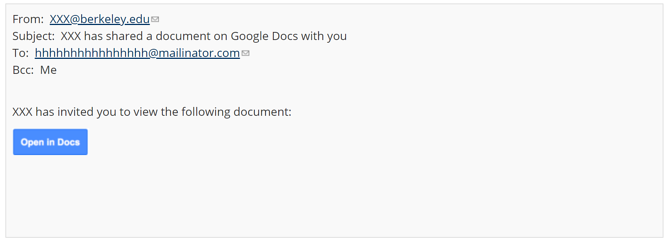
The traditional format of a phishing attempt typically involves using a malicious link sent to a user via email to download a malware file or extract information through a criminal website disguised as a trusted one. The trouble with this from a hacker’s point of view is that most major email service providers such as Google and Microsoft now scan every email for such malicious links. Emails with such links are either sent to the spam folder or boldly flagged to users as potential security risks.
To get around this, cyber-criminals have started exploiting messaging services typically used by business such as Slack, Facebook Messenger, and Skype. If they are able to steal user login credentials, they can pose as trusted team members and send malicious links to unsuspecting colleagues, who are more likely to fall for the scam because there is a familiar face ostensibly attached to it. There is not much data available yet on the exact scale of this scam tactic, but it is safe to assume that using collaboration tools as phishing vectors results in a much higher strike rate for cyber-criminals than the plain old email scam.
The Facebook messenger virus is a notorious tactic used by threat agents to spread cyber infections with the help of the Facebook Messenger app. The infected Facebook Message delivers a shortened link, e.g. video.bz or video_12345.bz, and an intriguing phrase that includes the name of the recipient and a couple of emojis. The embedded link seems to be leading to a YouTube or video link but once clicked, the malicious URL redirects to a phishing website filled with installers of dangerous browser extensions, fake Flash Player Updates, and similar content.
Also, in April, block chain platform Zilliqa announced phishing attacks using the brand name to target users of the platform and requesting details such as name, email, password, private key, etc. The attackers, “Zollo” who claimed to have entered into a partnership with Zilliqa used numerous platforms to reach out to potential targets including a fake Zilliqa blog, Zollo website, and Telegram.
To counteract this threat, businesses need to educate their employees about the realities of phishing, specifically on the point that any platform at all can become a dangerous phishing vector in the wrong hands. Typically, team members tend to be far more trusting of links shared on an internal Slack workplace than via email. They need to be taught that there is little difference between the two and that all a cyber-criminal need is an opportunity. If possible, businesses may also install third-party security add-ons to use alongside such programs to reduce the risk of scam vectoring.
Direct Interaction Phishing
As mentioned earlier, the entire raison d’etre of phishing is that the weakest point of any network security setup is the end user. Regardless of the different delivery and vectoring tactics, all phishing ultimately depends on the gullibility of the user. Direct interaction phishing takes this basic idea to the next level by exploiting available information from leaked databases to create highly personalised and believable messages to target marks. When the mark responds to the message as planned, they are then placed in direct communication with the cyber-criminal, who is then able to convince them to voluntarily hand over valuable data such as personal financial information and information that can be used to carry out identity theft.
In a typical scenario, the cyber-criminal may clone the website of a trusted institution such as a bank, and then use a live chat feature to get unsuspecting users to visit this website and submit financial details such as their credit card number, transaction history, social security/national insurance number and bio-data. This popular scam also works via telephone, for example with the criminal pretending to be the mark’s boss or colleague, and it is particularly effective when used on vulnerable demographic groups and non-internet savvy people.
Some weeks ago the Irish Times reported the story of a broadband fraud that left one family €15,000 poorer. The scammers employed a vishing tactic and pretended to be representatives of Telecoms company, Eir. They were able to get the victim to download a piece of software that gave them remote access to her laptop and further convinced her to go into her email and into her online banking platform. Even though they did not ask for any personal details or any details of access codes for her online banking, they did not need to as they could see everything she was doing on her laptop as she typed.
Counteracting this is a two-step operation. First of all, businesses need to educate their employees about what information should never be shared over the telephone or a live online chat. Banks are often at pains to point out for example, that they will never contact a customer and ask for key credit card details over the phone. Regardless of how well-personalised a phishing message is, a properly educated user will know that under no circumstances should they give up certain information via phone, email or text.
The second step is the introduction of a “channel switching” internal company communication protocol. What this means is that if a request for certain information comes via an official channel like email, the recipient should confirm that the purported sender actually requested this information using a different channel like Slack or text message. The idea is that it is considerably harder for a hacker to gain control of several official channels, so using different channels to confirm information requests functions as a type of 2-factor authentication.
SaaS-Focused Phishing
What this sort of phishing does is that instead of asking for information that has an obvious incentive to a cyber-criminal such as credit card numbers, it seeks to grab login credentials for SaaS (Software as a Service) packages like AWS, Slack, Google G-Suite and Dropbox. If they are successful, their impact can be devastating, potentially granting the criminal access to the entire data bank of business, or a complete record of its emails. It also helps the criminal pose as a trusted actor within the organisation and widens the phishing attack.